To authenticate lossy multimedia streams, tolerating packet loss is paramount. Our solution is to generate a sequence of keys through a sequence generated through pseudo-random function applications. We denote consecutive applications of the pseudo-random function as . By convention, . The sender picks a random and pre-computes a sequence of key values, where , and . We call this sequence of values the key chain. Each looks pseudorandom to an attacker; in particular, given , the attacker cannot invert and compute any for . On the other hand, the receiver can compute all from a it received, where , since . Hence, if a receiver received packet , any subsequently received packet will allow it to compute and and verify the authenticity of . This scheme tolerates an arbitrary number of packet losses.
Similarly, dropping unsafe packets (i.e. those packets where the security condition does not hold) does not cause any problems in the authentication of later packets.
In the basic scheme I, an adversary might try to capture two consecutive packets
before the recipient received the first of them, and then forge the packet
stream. Although the security condition prevents this, the key chain also
prevents this attack, because the initial commitment commits to the entire key
chain and it is computationally infeasible for the attacker to invert or find
collisions in the pseudo-random function.![]()
An additional benefit is that the key commitment does not need to be embedded in each packet any more. Due to the intractability of inverting the pseudo-random function, any value of the chain is a commitment for the entire chain. Hence the commitment in the initial authenticated packet is sufficient. Figure 2 shows an example of scheme II.
Kim2 Kim1 Ki Kip1 F f
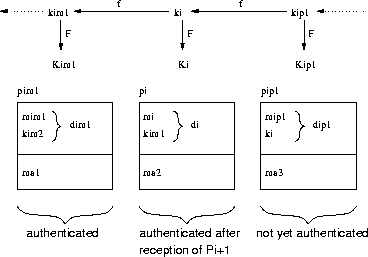
Figure 2: Scheme II. The packet format is the same as in
scheme I, except that the commitment is omitted and the keys
form a one-way key chain.