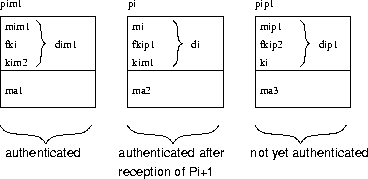
Figure 1: Basic stream authentication scheme. stands for message , is packet , denotes the secret key , are pseudo-random functions, and computes the MAC of packet using the secret key .
Here is a summary of scheme I: The sender issues a signed commitment to a key which is only known to itself. The sender then uses that key to compute a MAC on a packet , and later discloses the key in packet , which enables the receiver to verify the commitment and the MAC of packet . If both verifications are successful, packet is authenticated and trusted. The commitment is realized via a pseudorandom function with collision resistance. More details on the requirements on the pseudo-random functions are in appendix A. This protocol is similar to the Guy Fawkes protocol [1].
pim1 pi pip1 mim1 mi mip1 fki fkip1 fkip2 dim1 di dip1 kim2 kim1 ki kip1 ma1MAC ma2MAC ma3MAC

Figure 1: Basic stream authentication scheme.
stands for message , is packet , denotes the
secret key , are pseudo-random functions, and
computes the MAC of packet using the secret
key .
We now describe the basic scheme in more detail. The scheme is depicted in Figure 1. We assume that the receiver has an authenticated packet to start with (where ). The fields have the following meanings. is the message contained by the packet, is the secret key used to compute the MAC of the next packet, and commits to the key without revealing it. The functions and are two different pseudo-random functions. Commitment value is important for the authentication of the subsequent packet . To bootstrap this scheme, the first packet needs to be authenticated with a regular digital signature scheme, for example RSA [27].
To send the message , the sender picks a fresh random key and constructs the following packet , where and the computes a message authenticating code of under key .
When the receiver receives packet , it cannot verify the MAC instantly, since it does not know and cannot reconstruct . Packet (where ) discloses and allows the receiver first to verify that is correct ( equals the commitment which was sent in packet ); and second to compute and check the authenticity of packet by verifying the MAC of packet .
After the receiver has authenticated , the commitment is also authenticated and the receiver repeats this scheme to authenticate after is received.
This scheme can be subverted if an attacker gets packet before the receiver gets , since the attacker would then know the secret key which is used to compute the MAC of , which allows it to change the message and the commitment in and forge all subsequent traffic. To prevent this attack, the receiver checks the following security condition on each packet it receives, and drops the packet if the condition does not hold.
In order for the receiver to verify the security condition, the receiver needs to know the precise sending schedule of packets. The easiest way to solve this problem is by using a constant packet rate. The sending time of packet is hence where is the time on the sender's clock and is the packet rate (number of packets per second). In that case, the security condition which the receiver checks has the following form: , where stands for the arrival time (on the synchronized receiver's clock) of packet . The main problem with this scheme is that, in order to satisfy the security condition, the sending rate must be slower than the network delay from the sender to the receiver. This is a severe limitation on the throughput of the transmission. In addition, the basic scheme cannot tolerate packet loss. In particular, once a packet is dropped no further packets can be authenticated. We now gradually extend the basic scheme to eliminate these deficiencies.