

In order for HVAs to be useful for secure applications, we illustrate a variety of desired properties for HVAs. A HVA that is used in a particular application will only need to satisfy a subset of the properties. We will give several examples of these applications and their usage of the HVAs in the later section.
Near-one-way property
We define two images and to be near, denoted as , if the two images are perceptually indistinguishable.
It is difficult to devise an algorithm which can judge automatically whether two images are near since that depends on the person comparing the images. But in general, we can find some similarity-metric function and a threshold such that if , then the two images and are not near. Finding a good function for is an active area of research in image retrieval and is not in the scope of this paper.
Regularity property
Humans are good at identifying geometric objects (such as circles, rectangles, triangles, and lines), and shapes in general. We call images, which contain mostly recognizable shapes, regular images. If an image is not regular, i.e. does not contain identifiable objects or patterns, or is too chaotic (such as white noise), it is difficult for humans to compare or recall it.
We suggest two ways for testing the regularity of an image automatically.
To illustrate how to use energy in the magnitude spectrum of the Fourier transform in order to decide regularity, we show in figure 1 white noise along with the Fourier transform.
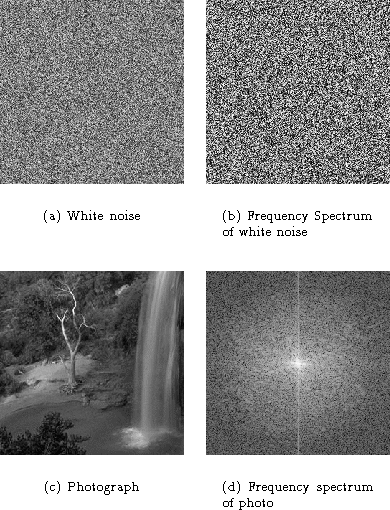
Figure 1: White noise and photograph
Minimum complexity property
Since the image might be presented in many different ways, i.e., printed in a newspaper, displayed on a color LCD display, or on a TV screen, the result of comparing two images needs to be robust with respect to resolution and color changes: if two inputs and are different, then the two outputs and should not be near with any resolution and color configuration that could occur in the secure system; similarly, if two inputs and are equal, then the outputs and should be near with any resolution and color configuration that could occur in the secure system.
An immediate implication of this property is that an image can not be too simplistic in shapes and patterns, or rely on subtle color differences. Just like for to the regularity property, we could use compression or the frequency spectrum to detect images that are simplistic. For example, compressing an image which has all pixels set to a unique color, should result in a very short file. Also, the frequency spectrum of such a simplistic picture has all the energy in the lowest frequency components.