An important requirement of our scheme signature scheme is that the receiver can continuously verify the signature of packets. Clearly, the receiver can only verify the signature once it can trace the authentication links to a signature packet. Hence, the verification delay depends on the frequency and the transmission reliability of signature packets. The signature packet rate depends on the available computation and communication resources. If we use -bit RSA signatures, a dedicated server can compute on the order of signatures per second. The corresponding communication overhead is bytes for the signature plus bytes for each hash included.
We also performed simulations with signature packets. The parameters included
the signature rate, the loss probability of signature packets,![]() and the
number of hashes per signature packet. Figure 11 shows the
sawtooth-shaped verification probability for a stream with packet loss
(bursty loss), the average burst length of dropped packets is , the hash is
split up into chunks of bits each (spanning a maximum length of
packets), hence chunks are necessary to verify a packet, which gives us
bits of the signature. The communication overhead per packet is therefore about
bytes per packet. The signature packets are sent every packets and
they contain -bit hashes of packets, and one -bit RSA digital
signature which amounts to bytes. Each signature packet is sent twice, so
the loss probability of a signature packet is reduced to . The average
per-packet overhead in this case is bytes.
and the
number of hashes per signature packet. Figure 11 shows the
sawtooth-shaped verification probability for a stream with packet loss
(bursty loss), the average burst length of dropped packets is , the hash is
split up into chunks of bits each (spanning a maximum length of
packets), hence chunks are necessary to verify a packet, which gives us
bits of the signature. The communication overhead per packet is therefore about
bytes per packet. The signature packets are sent every packets and
they contain -bit hashes of packets, and one -bit RSA digital
signature which amounts to bytes. Each signature packet is sent twice, so
the loss probability of a signature packet is reduced to . The average
per-packet overhead in this case is bytes.
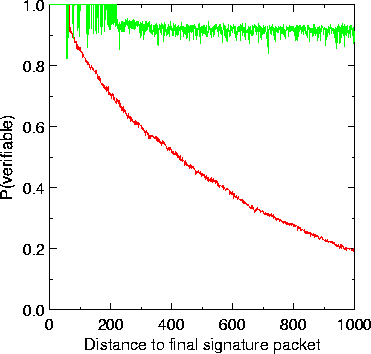
Figure 11: The verification probability for the extended scheme including
periodic signature packets.