In this experiment, we use a simple, linear metric function. Each operation has a unit-cost. The cost value of a protocol is the sum of the costs of all the protocol operations and components. We choose UNIT_ELEMENT_COST (cost to send a nonce or a principal name), and NEW_NONCE_COST (cost to generate a new nonce). For symmetric-key protocols SYM_ENCRYPTION_COST (cost to encrypt a message with a symmetric key), and for asymmetric-key protocols ASYM_ENCRYPTION_COST (cost to encrypt a message with an asymmetric key).
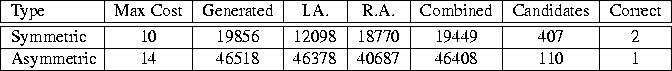
Table 1 shows the statistics for the protocol generation. The cost threshold is 10 for symmetric-key authentication protocols and 14 for asymmetric-key protocols. The column labeled ``Generated'' shows how many protocols were initially generated with the corresponding cost threshold without applying the intruder reduction. The table depicts the effectiveness of the impersonator and replay attacks. The column marked ``I.A.'' shows the number of protocols that are eliminated by the impersonation attack. Similarly, the ``R.A.'' column depicts the number of protocols that are vulnerable to the replay attack. The combination of the two attacks is quite efficient (shown in the ``Combined'' column) and leaves about 2% of candidate protocols for the symmetric case and 0.2% for the asymmetric case (shown in the ``Candidate'' column). The running time for the protocol generation is on the order of 1 second for every 2000 protocols generated which includes the pruning algorithm (this number is based on our Java implementation, executed by the JVM of the Sun JDK 1.1.7, running on a 400 MHz Pentium II Linux workstation).
Table 1: Experiment Statistics for protocol generation. I.A. stands for
impersonation attack and R.A. for replay attack