Figure 5: Tree updating in partition operation
Figure 4: Partition Protocol
Assume that a network fault occurs in a group with members . From the viewpoint of each remaining member, this appears as a concurrent leave of multiple members. Our partition protocol is a multi-round protocol which runs until every member computes the new group key.
In the first round, every remaining member updates its tree by deleting all partitioned members and their respective parent nodes. The procedure for deletion is as follows:
All leaving nodes are sorted in the order of depth. Starting at the deepest level, each pair of leaving siblings is collapsed into its parent which is then marked as leaving. This node is re-inserted into the leaving nodes list. This is repeated until all leaving nodes are processed.
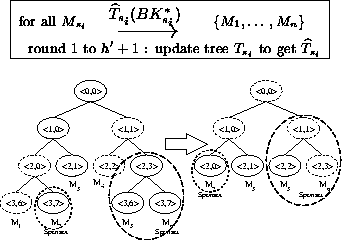
The resulting tree has a number of leaving (leaf) nodes but every such node has a remaining sibling node. Now, for each leaving node we identify a sponsorusing the same criteria as described in section 5.3.
Each sponsorthen computes the keys and blinded keys on its key-path as far up the tree as possible. Then, each sponsorbroadcasts the set of new blinded keys. Upon receiving a broadcast, each member checks whether the message contains a new blinded key. This procedure iterates until all members obtain the group key. (A member can compute the group key if it has all the blinded keys on its co-path.)

Figure 5: Tree updating in partition operation
Figure 4: Partition Protocol
To prevent reusing the old group key, one of the remaining members needs to change its key share. In the first round of the partition protocol the shallowest rightmost sponsorchanges its share.
Figure 5 shows an example where all remaining members delete all nodes of leaving members and compute the keys and blinded keys in the first round. In the figure on the right, and cannot compute the new group key, since they lack the blinded key . However, broadcasts in the first round. Hence, every member knows all blinded keys and can compute the group key. As explained above, before computing , changes its share .
If a member computes the group key in round , then all other members can compute the group key, at the latest, in round , since 's broadcast message contains every blinded key in the key tree. Hence, every member can detect the completion of the partition protocol independently.