Figure 2: Key management protocol with sender's key
The previous architecture makes Trent, the server, a hot spot, since every message must be decrypted by Trent to verify authorization and re-encrypted it again to preserve confidentiality. This architecture allows a sender to send multicast messages directly to the group.
To satisfy sender authorization requirement, we made the following simple hack:

Figure 2: Key management protocol with sender's key
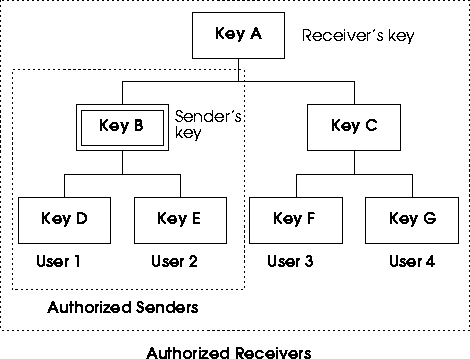
We strategically place all authorized senders under one subtree (the subtree under Key B) which is separate from the rest of the members who are authorized to receive messages only. The sender's key (in this case Key B) is assymetric (K.Sender.priv, K.Sender.pub). K.sender.priv, known by authorized senders only (User 1 and 2), is used for signing the message. K.sender.pub, known by all members in the group, is used for verifying that the message is sent by authorized senders.
This assymetric sender's key is updated everytime an authorized sender joins or leaves the multicast group. The server also needs to broadcast the new sender's public key (K.Sender.pub) to the rest of the group by encrypting it with the group key ({K.Sender.pub}K.Group).
Now the rest of the protocol becomes simple:
Alice -> Group: [ {M}K.Group, {H(M)}K.Sender.priv ]
All the properties in the original architecture are preserved here. Integrity is guarenteed by the hash, which is in turn protected by the sender's private key. Sender authorization is achieved because only authorized sender can produce the signature. Confidentiality is preserved because it is encrypted with the group key.
Authenticity retains the similar meaning as the original architecture, namely ``the sender of the message was authenticated by the key management server as one of the authorized senders of this multicast group''.
Sender anonymity is stronger in this architecture, because the sender Alice does not need to expose her own identity to Trent to send a message. She can just sign the message and the rest of the multicast group will accept her message. Receiver privacy remains unchanged in this case.